What is IAM and Why it's Important ?
Identity and Access Management • Introduction
This is the most demanded and important concept to learn in AWS. It is required whether you're working or a student or whatever role you're playing in Cloud. It is considered fundamental knowledge.
Introduction
IAM refers to a framework or policies and technologies for ensuring that the proper and authorized people in an organization have the appropriate access to technology resources.
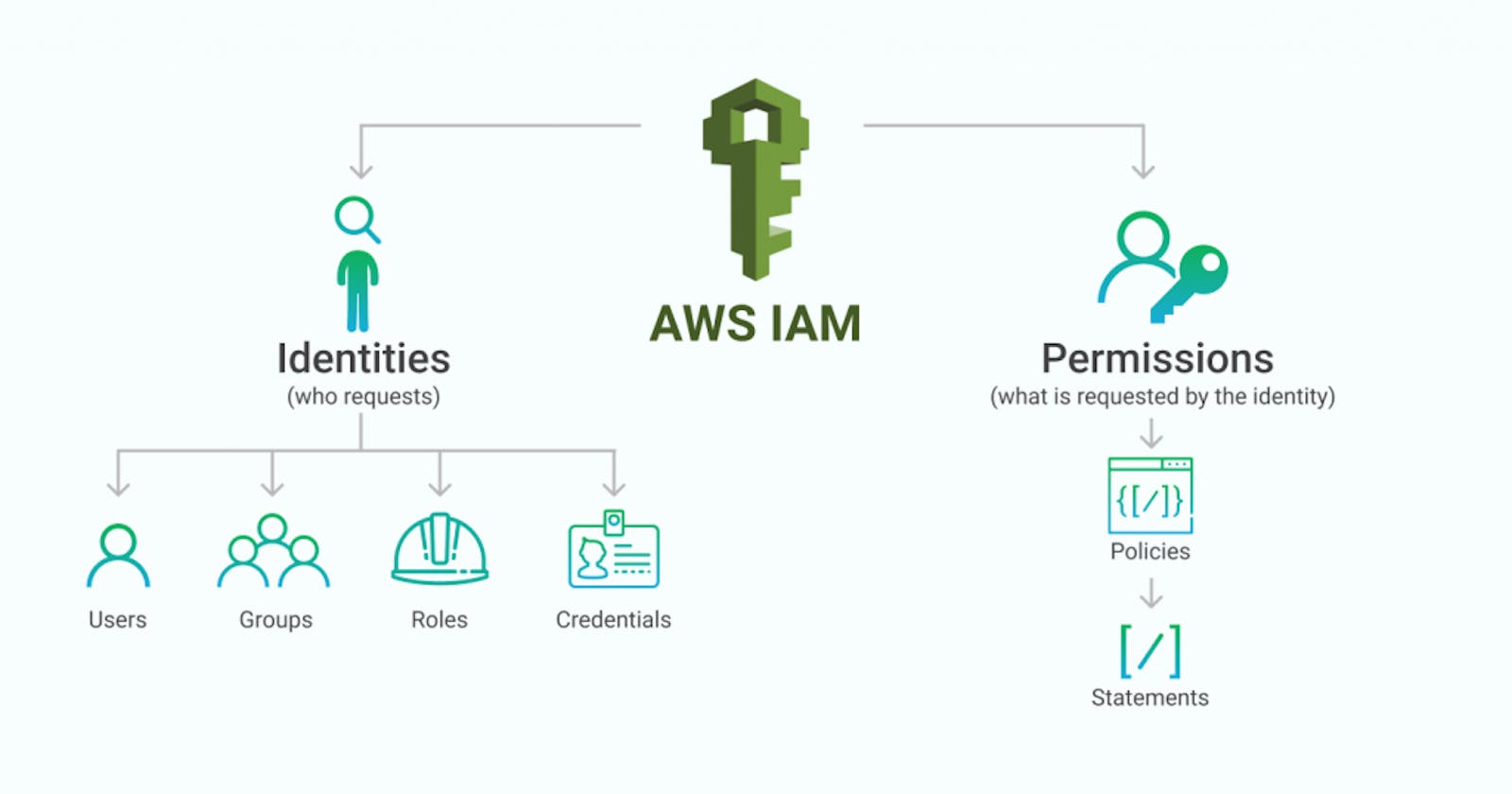
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. You can use IAM to control who is authenticated (Signed-In) and authorized (has permission) to use Resources.
For example, if there is a developer then we will assign only those resources which are required for development such as permission to use Amplify & Lambda Function. Similarly, for other people/employees.
When you first create an AWS account, you begin with a Single Sign-In identity that has complete access to all AWS Services and Resources in the account.
The identity is called the AWS account 'Root User' and is accessed by Signing in with the email address and password that you used to create the account.
AWS Strongly recommends that you do not use the root user for your everyday task, even the administrator ones.
Use other IAM user account accounts to manage the administrator task of your account and securely lock away the root user Credentials and use them to perform only a few account and service management tasks.
AWS IAM is a feature of your AWS account offered at no additional charges. You will be only charged only for the use of other AWS products by your IAM users.
Note:
IAM is a global AWS Service. It's not region specific.
The IAM user limit is 500 per AWS account. You can add up to 10 Users at one time.
You're also limited to 300 groups per AWS account.
You're limited to 1000 IAM roles under AWS Account.
The default limit of managed policies attached to an IAM Role and IAM user is 10.
IAM Users can be a member of 10 Groups (maximum).
We can assign two access keys (max) to an IAM user.
Features of IAM
Shared access to your AWS Account
- You can grant other people permission to administer and use resources in your AWS Account without having to share your access credentials (root password or access key).
Granular Permission
You can grant different permission to different people for different Resources.
For instance, you can allow some users complete access to EC2, S3, DynamoDB, and Redshift while for others you can allow read-only access to just some S3 buckets or permission to administer your EC2 instances or to access your billing information but nothing else.
Secure access to AWS Resources for applications
You can use IAM features to securely give applications that run on AWS. Let's say your application is running on EC2 instances. the credentials that they need to access other AWS resources. Examples include S3 bucket and RDS or DynamoDB databases.
You don't want to permit the user to access the connected resources to AWS EC2 so we can apply for such permission as well to secure our application.
Multi-Factor Authentication (MFA)
You can add two-factor authentication to your account for individual users for extra security you can use physical hardware or virtual MFA, for example, Google Authenticator.
Identity Federation
Identity trusting on 3rd party application to use the AWS account. it's the kind of oAuth authentication.
If you don't want to create multiple users so to do that you have created your identity federation by using the LDAP server or Active Directory all can also use 3rd party applications such as Facebook or Google to authenticate the users to access the AWS resources for your users.
You can allow users who already have passwords elsewhere. For example in your corporate network or with an internet identity provider to get temporary access to your account.
Identity Insurance for assurance
If you use AWS Cloudtrail, you recieve logs of all the events associated with your AWS account with its services and associated resources.
PCI/DSS Compliance
- IAM supports the processing, storage and transmission of Credit Card by a merchant or Service provider and has been validated as being compliant with Payment Card Industry (PCI) Data Security Standards (DSS)
Eventually Consistent
If a request to change some data is successful, the change is committed and safely stored however the change must be replicated across IAM which can take some time.
IAM achieves high availability by replicating data across multiple servers within AWS datacenter around the world.